The following document explains the hardening strategy of Athento's cloud service. This strategy revolves around 4 main areas.
1. Identification of security risks
Athento has ethical hacking certifications and execution planning. Periodically, the planned execution of penetration tests is carried out in order to extract the final report with possible physical, network or application problems that may be subject to attacks and thus apply corrections and/or changes on the hardening strategies that we will see below.
The motivations for carrying out regular ethical attacks are:
- Obtain a temporary snapshot of the overall safety status.
- Ensure minimum risk in pre-production passes.
The following graph shows the phases of ethical hacking executed by Athento.
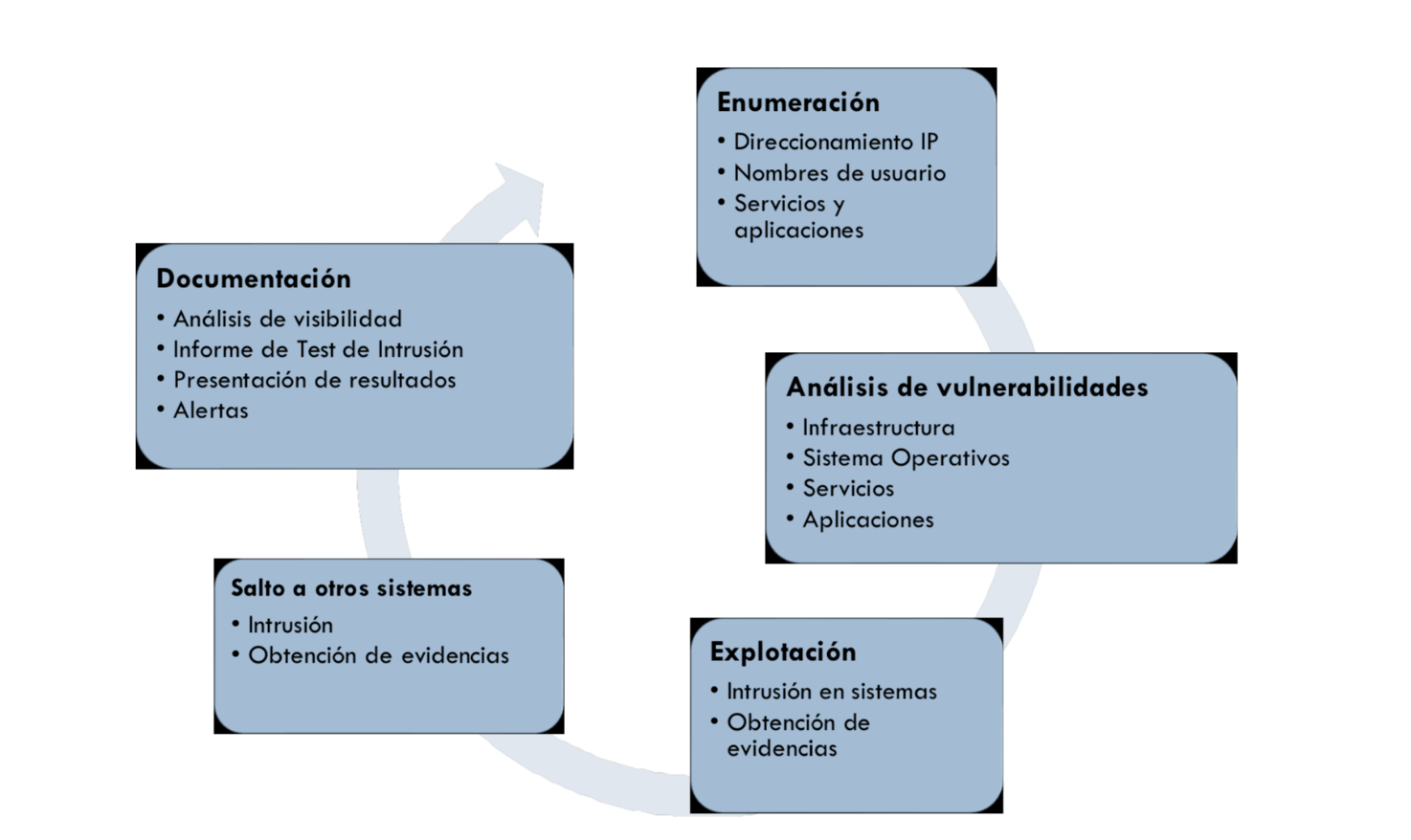
The actions carried out are as follows:
- Vulnerability audit
- Pentesting
The aforementioned actions are carried out in accordance with the following methodologies:
- ISECOM OSSTMM 3.0
- OWASP
- NIST SP 800-42, 800-115
- ISSAF
- Penetration Testing Framework
- PTES
In addition to Athento's automated or manual tests, our cloud is tested by the security departments of some of our customers, which are large corporations that care about their documents.
2. Infrastructure and service protection
The following is a description of the different security layers that apply to our service and the infrastructure that hosts it (some of them are only available on demand and depending on the infrastructure provider):
2.1 Physical Security Level
- Datacenters with a high level of physical security.
- Physical access controls.
- Fire control.
- Network security.
- Security control of servers for proper operation.
- Replicated electrical systems.
- Geographic separation.
- Connectivity options that allow private or dedicated connections from your office or local environment.
- Office or local environment.
- etc.
2.2 Cloud hosting characteristics
Athento has datacenters and cloud services that offer intrinsic protection, from the physical point of view in dedicated server services in OVH, to security levels in virtualization services and access in Azure or Amazon Cloud.
The general characteristics of the different providers used by our cloud service are described below.
- Azure: Athento's architectural solutions mounted on Azure present the security features intrinsic to the provider itself. In this way, Athento ensures that layer of security control in all its services. In addition, given the features and components that Azure includes to be able to perform security controls (NSG), Athento includes the necessary layers to obtain a minimum risk as we have indicated above.
- OVH: Athento has dedicated server services to mount its solutions. From OVH the systems have a high level of physical security and attack control to maintain the established network service levels, but they do not have security layers (at machine and services level) and in this sense from Athento we apply the security policy at server level.
- AWS: The security available on AWS is one of the provider's priorities. As in Azure, AWS has monitoring and protection services for the flow of information that travels to the platform where Athento deploys its services.
2.3 Network and communication security
- Perimeter: DNS control to control and discover domains that point to available systems and/or services and secure them. Athento performs TLDs and RIR control processes to secure the public perimeter when it is performed in the Internet environment. Among the tools used by Athento are: Sublist3r, Aquatone and SpiderFoot.
- VPN: Athento establishes VPNs to provide secure access and communication between clients for updates and controlled access. Among the types of VPNs offered are site-to-site for organizations, or point-to-site controlled access for specific access to secure accounts.
- Firewall: Athento counts with the activation of firewalls to establish IP filtering between the established services and communication port status control.
- Anti-DDoS protection.
- Confidentiality of data.
- Los firewalls de red integrados.
- Encryption in transit with customer-controlled TLS on all services.
- Connectivity options that allow you to establish private or dedicated connections from your office or local environment.
- Automatic encryption of all traffic on regional and global networks.
2.4 Operating System
Athento has a policy of automatic updates of its operating systems, usually Ubuntu in its latest LTS. In this sense, there is security package update control to keep the systems up to date in their security versions.
2.5 Web server level security
- Secure configuration: For securing Apache, Athento has a set of configurations to prevent possible publication of information that could help the attacker.
- HTTPS: TLS encryption in communications while maintaining secure protocols and cipher suite.
- Apache Modsecurity: Web application firewall that provides protection against various attacks on Web applications and allows HTTP traffic monitoring and real-time analysis without the need to make changes to the existing infrastructure. modSecurity filters attacks by XSS, SQL Injection, anomalous behavior in protocols, robots, Trojans, LFI, etc. and also incorporates specific rules.
- IP filtering: in the definition of the virtualhost used as proxies, security rules are established, including the inclusion of IP filtering.
- Elimination of unnecessary ports and services: in penetration tasks Athento detects unnecessary ports and services that are eliminated and/or closed.
2.6 At Athento level
In general, Athento applies measures such as those described below:
- Control of brute force attacks.
- Blocking malicious applications.
- SQL Injection
- Stored data encryption: blobs and binaries.
- Password control
- Auditing tools (security logs, document movement logs).
Next, we will see in more detail some of the security mechanisms defined at the level of the layers of the application itself.
- Django: Django offers security mechanisms at the Cro level, Cross site request forgery (CSRF), SQL injection protection, Clickjacking protection, SSL/HTTPS, Host header validation, Session security, User-uploaded content y otras medidas. More information at https://docs.djangoproject.com/en/2.2/topics/security/
- Connection with PostgreSQL: Access control through user rules and IP filtering.
Repository encryption: Athento has the ability to encrypt the repository using a secret key or certificate. - Hotfixing: Athento has a policy of updating localized hotfixes to solve localized security problems at CVE or internal level.
Likewise, the management of platform authentication and password management deserves its own section:
Auth-chain
Within Athento's authentication and authorization layer, we can find a suite of authenticators that can be chained together in order to establish maximum security.
Password Policy
Athento has a password policy to establish the following security checkpoints:
- History of changes: password repetitions are controlled.
- Complexity and strong formatting: formatting rules are established with the inclusion of special characters and the mandatory use of capital letters and numbers.
- Is it possible to prevent users from reusing previously used passwords?
- Is it possible to manage the complexity of passwords in Athento?
- Is it possible to set the password length for users?
- Expiration time: expiration times are set to force password updates.
- Change notifications: a notification control is established after the change or change request.
- Encryption of passwords with secure algorithms.
- User blocking for failed authentication attempts
- Session control
3. Event monitoring or detection
Athento has monitoring systems at different levels, from the operating system (Ubuntu LTS 16+) to monitoring and access control in its applications.
3.1 Operating system monitoring
In the context of the operating system, access control policies are established in order to identify possible network attacks and detect possible intrusions (IDS) or possible denials of service or excessive bandwidth consumption. Among the tools we use for monitoring and identifying possible attacks, DDoS, or unauthorized access are:
- psacct/acct: control of what happens in our system to identify which users have entered the machine, actions performed, processes launched, and to be able to locate possible unauthorized executions and possible unauthorized access.
- Control sniffers.
- Tcpdump: malicious packet monitoring.
- TCP SYN (Stealth) Scan (-sS): for port identification and enabled services.
- Logwatch: system log analyzer to identify malicious operations on the system.
- Sysstat: system monitor to identify possible unexpected network loads and consumption.
These tools send messages to Athento's messaging systems with the reports obtained and are evaluated on a daily basis.
3.2 Monitoring of services and machines
In terms of server and service monitoring, Athento has a cloud monitoring system to verify the status of services and RUMs at 24x7 level to control the consumption and status of communications with the systems.
In addition, Athento has cloud performance monitors that report possible usage spikes or DDoS.
4. Responding to vulnerabilities
Among the security control practices that Athento has in its policies are vulnerability auditing and pentesting, as we indicated above. In the vulnerability audit we quantify and classify vulnerabilities and establish recommendations to make the necessary updates. As for the pentesting, we perform the detection of some known and some unknown vulnerabilities to establish the associated impact and resolve them quickly.
4.1 Detection and localization of vulnerabilities through fuzzing and pentesting
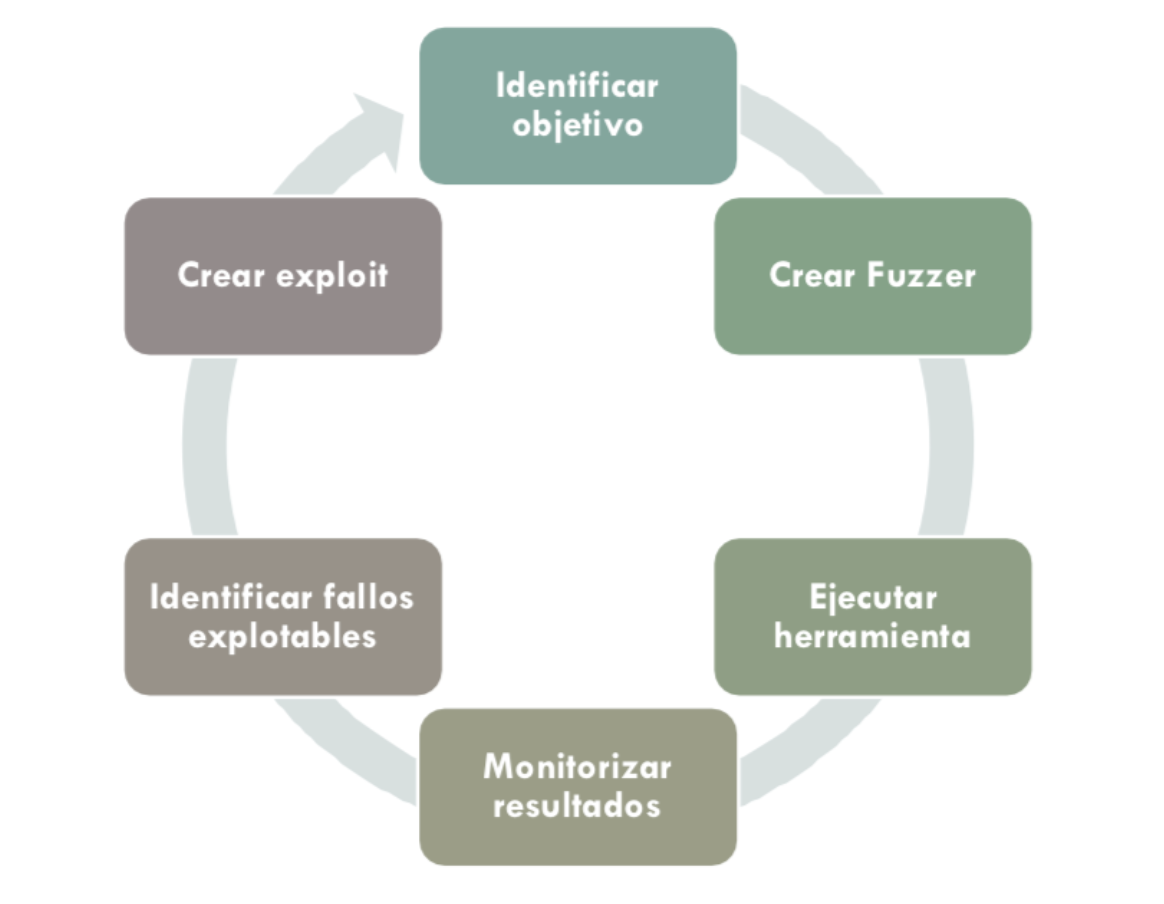
Athento actively searches for bugs and security vulnerabilities in its applications. To do so, it relies on automated market tools.
Some of the tools used are listed below.
Fuzzing Tools
- Frameworks: Spike, Peatch, Sulley
- Red: doona
- Ficheros: Filefuzz, Spikefile, zzuf
- Browser: Mangleme
Detection and localization tools
- Detectify
- Burp
- WebInspect
- Acunetix
- Nikto
- Skipfish
- Arachni
4.2 Security incident response
Athento has a Security Incident Management Policy that includes instructions on:
- How incidents should be reported
- Who is the person responsible for their management
- How it should be followed up
- To whom and within what timeframe the incident should be reported
Athento also has a management platform for incident logging.
4.3 Incident and vulnerability analysis
Our security team reviews all available monitoring systems to gather as much information about the incident or vulnerability as possible. This collected information is used to document the vulnerability or incident and for possible exploitation. Exploitation refers to the reproduction of the vulnerability or incident in order to fix it.
5. Recovery
Whether they are incidents reported because they have actually occurred or vulnerabilities detected in our vulnerability detection tests, Athento must act on them.
5.1 Exploitation of vulnerabilities
Once vulnerabilities are found, Athento reproduces or exploits them to find a solution.
Exploitation tools
- Mfsconsole
- Nessus
5.2 Data or document retrieval
If we are faced with a security incident that has resulted in data loss, the Backup and Recovery Policy takes on great importance.
Does Athento have backups and resources to restore and recover the system?
Comments
0 comments
Please sign in to leave a comment.